Part 1 – What is the problem
Part 2 – Installing a simple Linux Reverse Proxy on the same box ( 20 mins )
Part 3 – ( This Post ) Converting your Domino SSL Certificate to work with Apache (30 mins )
Thankfully this post is now obsolete – see this IBM article which includes a modern tool to manage the Keyrings
Note that the easiest option to install a verified SSL certificate into the Apache server is to buy a new one. However, if you have a copy of Windows XP handy you can convert your existing Domino SSL certificates to Apache certificates with the following scheme.
Many thanks to Darren Duke who helped get me started with this scheme via a post on his blog about a different but overlapping scenario.
Step 0 – Why do I need to do this
Essentially you need to get your private key because Apache needs it to verify the SSL certificate,
When you originally requested your verified SSL certificate from your SSL vendor you gave them a CSR which was created via the Domino Server Certificate Administration database.
This generated a private key and used that to create the CSR request.
The SSL provider took this and using their own encryption key created the SSL certificate. This certificate will only work in the presence of your original private key and Apache cannot use the Domino .kyr file format where it is buried.
Step 1 – Install IBM ikeyman version gsk5
You need this specific version. You can download it here
It will only run on Windows XP
a) extract the zip contents to the root of the c: drive
b) Run the batch command gskregmod.bat from the command line to set some registry settings
c) Run the batch command runikeyman to open the application.
Step 2 – Extract the Private Key and Cert information from Domino the keyring KYR file
a) open the .kyr file and export it as a P12 file

Step 3 – Convert the PK12 Format file to a text file
There are two methods here.
The simple one is to use this resource but I am never happy uploading private keys to the web.
The better method is to use the OpenSSL module already stored on your server.
Use WinSCP to copy the .PK12 file to the server and then use the following command in the Linux console
>openssl pkcs12 -in example.p12 -out example.pem
You will need to give the .PK12 password and supply a new one.
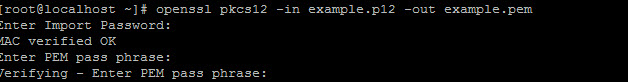
You can now open the pem file as a text file and can see that it has 4 components ( this may vary )
1) Server Certificate Intermediate Certificate
this is the public key for the intermediate certificate and could have been obtained from the SSL certificate issuer’s web site
2) Certification Authority Root Certificate
this is the root public key for the intermediate certificate and could have been obtained from the SSL certificate issuer’s web site
3) KeyPair
This is your SSL certificate and was probably emailed to you when you purchased your SSL certificate ( but it is no good without the private key buried in the Domino kyr file )
4) Encrypted private key
This is what you are after. I believe that you can use it in its encrypted form but you will need to provide the password every time you start Apache. To avoid this you can store it on the server in its unencrypted form but you need to make sure it is well secured otherwise a anyone who has access to it can compromise your SSL traffic.
Read section 6.6. of this document and apply the security settings recommended
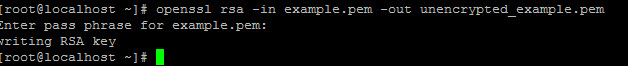
You can unencrypt the key using the following command
>openssl rsa -in example.pem -out unencrypted_example.pem
Step 5 – Deploying the Private Key and certificates
There are lots of article about how to deploy the files to Apache but this is the scheme that I used. There is another method that chains the root and intermediate into a single chain file.
a) save the intermediate certificate to the /etc/pki/tls/certs folder as a text file called intermediate.pem
You can extract the text from the file generated above or use the one sent to you when you purchased the SSL certificate.
b) save the root certificate to /etc/pki/tls/certs as a text file called root.pem
c) save your domain SSL certificate to /etc/pki/tls/certs as site_cert.crt or similar
d) save your unencrypted private key to /etc/pki/tls/private as site_private_key.pem or similar
e) modify the /etc/httpd/conf.d/ssl.conf file as follows ( allowing for any difference in file names )
SSLCertificateFile /etc/pki/tls/certs/site_cert.crt
SSLCertificateKeyFile /etc/pki/tls/private/site_private_key.pem
SSLCertificateChainFile /etc/pki/tls/certs/intermediate.pem
SSLCACertificateFile /etc/pki/tls/certs/root.pem
If you now issue the command >service hhtpd restart then the new certificates should be used.
If you are using the encrypted private key then you will be challenged for a password as shown below

That’s it. You have now converted your Domino SSL certificate for use with Apache. Collect $200 and pass Go.
